You open up your Web browser, just like any other day, but something’s not right. The page that always loads when the browser starts is different. There are shortcuts in your Favorites folder that you can’t recall putting there, and other abnormal things happen when you browse. Worst of all, even though you manually switch everything back to the original settings, the changes don’t stick. Or maybe the options to revert to the old settings aren’t even
there at all.
Your browser has been hijacked, and although most hijackers are not interested in destroying files or doing the malicious things associated with other attacks, such as that of viruses, a hijacked browser is still a major problem that must be handled immediately. Hijackers are designed to redirect your Web browser to Web sites of the hijacker’s choosing to direct more traffic to specific sites so that they can generate more advertising revenue.
Hijack Basics
Browsers may be hijacked in a number of ways. The most basic attack is triggered when you view a Webpage and code within that page (or code that is automatically downloaded when the page is viewed) uses a security loophole to change your default home page, default search page, and browser settings. It doesn’t do anything other than that, meaning you can fix the problem by changing those entries back to their original settings.
Many hijackers rely on users installing software, either inadvertently or on purpose, that gives them broader access to the system. Some of these hijackers prevent you from changing your home page or search engine back to what you want by completely disabling those settings in Internet Explorer. Others do even worse things, for instance, causing pop-up advertisements to appear even when you aren’t browsing the Web.
An Ounce Of Prevention
One of the easiest ways to practically eliminate the potential for being hijacked is to switch from Internet Explorer to an alternative Web browser such as Firefox 2 (free; www.mozilla.com/en-US/firefox) or Opera 9 (free; www.opera.com). Hijackers focus their efforts on IE because so many people use it, and programs designed to exploit flaws in IE won’t work when applied to other browsers. Firefox and Opera continue to gain in popularity, and this may increase to a point where those browsers become targets, as well. But for now, if you currently use IE, switching over to a different browser comes with immense security benefits.
If you use IE, make sure to keep it as up-to-date as possible because Microsoft constantly identifies and fixes security holes. To do so, open IE, expand the Tools menu, and click Windows Update. Click either Express
or Custom (or update the Windows Update software, if necessary) and install all of the patches that are available for Internet Explorer.
No matter what Web browser you use, it is extremely important to install multiple antispyware applications on your computer and regularly update them. These programs scan for current problems, and many of them also lock down the computer so hijackers can’t easily use the most common routes of entry. You can use as many antispyware applications on the same computer that you want to (unlike antivirus software, where you must stick to a single program). We recommend Windows Defender (free; www.mi crosoft.com/athome/security/spy ware/software/default.mspx), Spybot Search & Destroy (free; www.safernetworking. org), Ad-Aware (free; www.lavasoftusa.com), and SpywareBlaster (free; www.javacoolsoft ware.com/spywareblaster.html). Update these programs at least once per month if they don’t come with the ability to do so automatically.
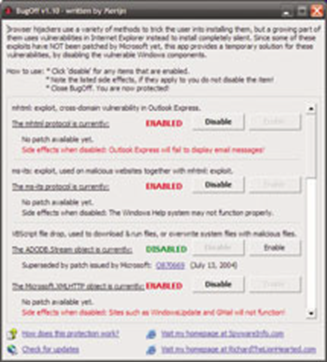
Also, we recommend downloading and running BugOff (free; www.spy wareinfo.com/~merijn/programs.php), which fixes a lot of exploits commonly used by hijackers. BugOff is trickier to use than the other programs mentioned because you must enable or disable entries manually and doing so can have impact on programs you actually want to use. When running BugOff, the goal is to click Disable for as many entries as possible but check the Side Effects text closely to make sure doing so won’t interfere with your applications.
For example, disabling the Microsoft.XMLHTTP Object closes a hole that a hijacker can use, but it also prevents Windows Update and Gmail from working properly, so leaving it enabled is probably worth the risk. Clicking the Disable button instantly makes the change, so simply close the program when you are finished.
Be very careful when using BugOff, or you may accidentally disable a legitimate program.
Use Windows Update and your Web browser as up-to-date as possible.
Finally, always be on your guard when browsing or clicking links in emails or other documents that open Web pages in your browser. The worst hijackers gain access to the computer because people unknowingly install them on their computers by clicking a button or link in a pop-up window that appears while browsing or by installing downloaded software that lets the hijacker get a piggyback ride onto the hard drive. Don’t blindly click links included in emails and never click anywhere in a pop-up advertisement (you can press CTRL-W to close an
IE window without having to click to close it). Also, be on the lookout for pop-ups that look like alerts from Windows but are actually disguises designed to get you to click a button, inadvertently giving your permission to download whatever the hijacker wants to install.
A Pound Of Cure
Heading off the hijackers doesn’t take a lot of work, but you have real problems if the browser has already been infiltrated. Before getting into specific fixes, it is important to note that the steps provided in this article apply to the latest version of Internet Explorer 7. If you use an earlier version of IE, you should upgrade to the latest version or
use an alternative browser for security reasons.
If you’re lucky and the hijacker simply changed your IE settings without installing any other software on your computer, you can easily revert to the settings you want to use. To establish the default home page, open IE, navigate to the page you want to use for a home page, expand the Tools menu, click Internet Options, and select the General tab. Click Use Current, and the page you navigated to becomes the default home page, or you can enter it manually (such as entering www.google .com if you want to use Google as your home page). Click Apply when you’re finished.
Click the Settings button in the Search section to re-establish your default search settings. Click to highlight the incorrect search entry, click Remove, and then highlight the entry you want to use and click Set Default. Click OK. If the search service you want to use doesn’t appear on the list, click Find More Providers, click the entry for the service you want to add, follow any prompts that are provided (if any), and the service should now be available when you establish default settings. There is also a Create Your Own option on this page that lets you add any search service that isn’t represented on Microsoft’s master list.
If you think your browser has been hijacked, checking to see if the culprit is the oft-used CoolWebSearch hijacker
or one of its myriad offshoots should be your first priority. These hijackers are designed to drive Web traffic to www.coolwebsearch.com (don’t type that address into your Web browser!) or other advertising sites. They accomplish this using many means, ranging from making the computer think that popular sites such as Yahoo! Search don’t exist (and instead redirecting you to an ad site) to making IE think that restricted Web sites should be trusted.
There is much more you can do to protect yourself from hijackers. It is important to keep in conscious mind while using browsers. Stay tuned be dropping your email in the sign up box below.















0 comments