If you connect to the internet at unsecured WiFi hotspots, like say your favorite coffee shop or book store, then you have always been at risk of the vulnerability exploited by Firesheep. So what exactly is this vulnerability? It’s easiest to understand by way of an example where we’ll use Facebook but be aware that they are only one of many popular websites, including Twitter and Flickr, to use this method.

To connect to Facebook, you log in with your Facebook user name and password. Then, once your credentials have been checked, you establish a private session with Facebook. No problem, right? Wrong! Let’s take a look at what is actually being transmitted back and forth across the network.
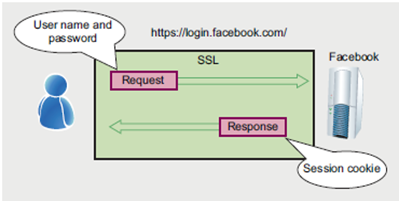
Here we see what happens when you log in to Facebook. So far so good – your user name and password are protected by a Secure Sockets Layer (SSL) connection. But note that the Facebook server answers back with a session cookie which is simply an identifying number that your browser stores for the duration of the session. So here the vulnerability rears it’s ugly head. Notice that when you request a page from Facebook – that’s any page including your profile page – Facebook asks your browser for the session cookie. If it matches the session cookie that it sent you when you logged in then it will happily serve up the page. In particular, notice that when your browser responds with the session cookie it is completely in the clear. Viewable and usable by anyone eavesdropping on your conversation with Facebook. So all a bad guy has to do is steal your session cookie – in fact it’s not even really stealing since it’s out there in the open – and use it to make Facebook think that it’s talking to you.
This exploit is commonly referred to as HTTP session hijacking or side-jacking and, as mentioned earlier, it’s been known and used by bad guys for a very long time. Up until now it required some modicum of expertise
on the part of the hacker to accomplish a side-jacking attack. The attacker had to use a packet sniffer to capture all those packets flying around, decode the packets to find session cookies in the clear and then create spoofed session cookie responses to join your session. For experienced hackers this wasn’t terribly challenging since they usually had software that would automate the process. The saving grace, so to speak, was that most experienced hackers weren’t terribly interested in Facebook pages or Twitter tweets.














0 comments